Based On API
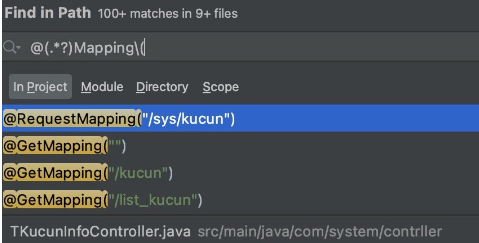
For example, if the target program uses SpringMVC, we can use annotation to find the entrace functions. I.E. Globally search “@(.*?)Mapping(” so that it can match @RequestMapping, @GetMapping
Based on Dangerous Functions
According to the dangerous functions, then reverse the process to find source. (Function entrance)
For example, if we want to find deserialization vulnerability in the Java, we can find following functions:
ObjectInputStream.readObject
ObjectInputStream.readUnshared
XMLDecoder.readObject
Yaml.load
XStream.fromXML
ObjectMapper.readValue
JSON.parseObjectBased on Functionality
First locate the vulnerable functionality according to the experience, then use blackbox/whitebox to find related issues.
Based on Third Party
Look at pom.xml and configuration files to see if all third party components are up to date.
Based on Tools
Uses both fuzzing and static analysis tool to have an initial scan. Then manually check with each alert.